Domain Name System: Why Always Me?
You’re not dumb—you just might not have all the prerequisites yet. -Lelouch
Mindmap
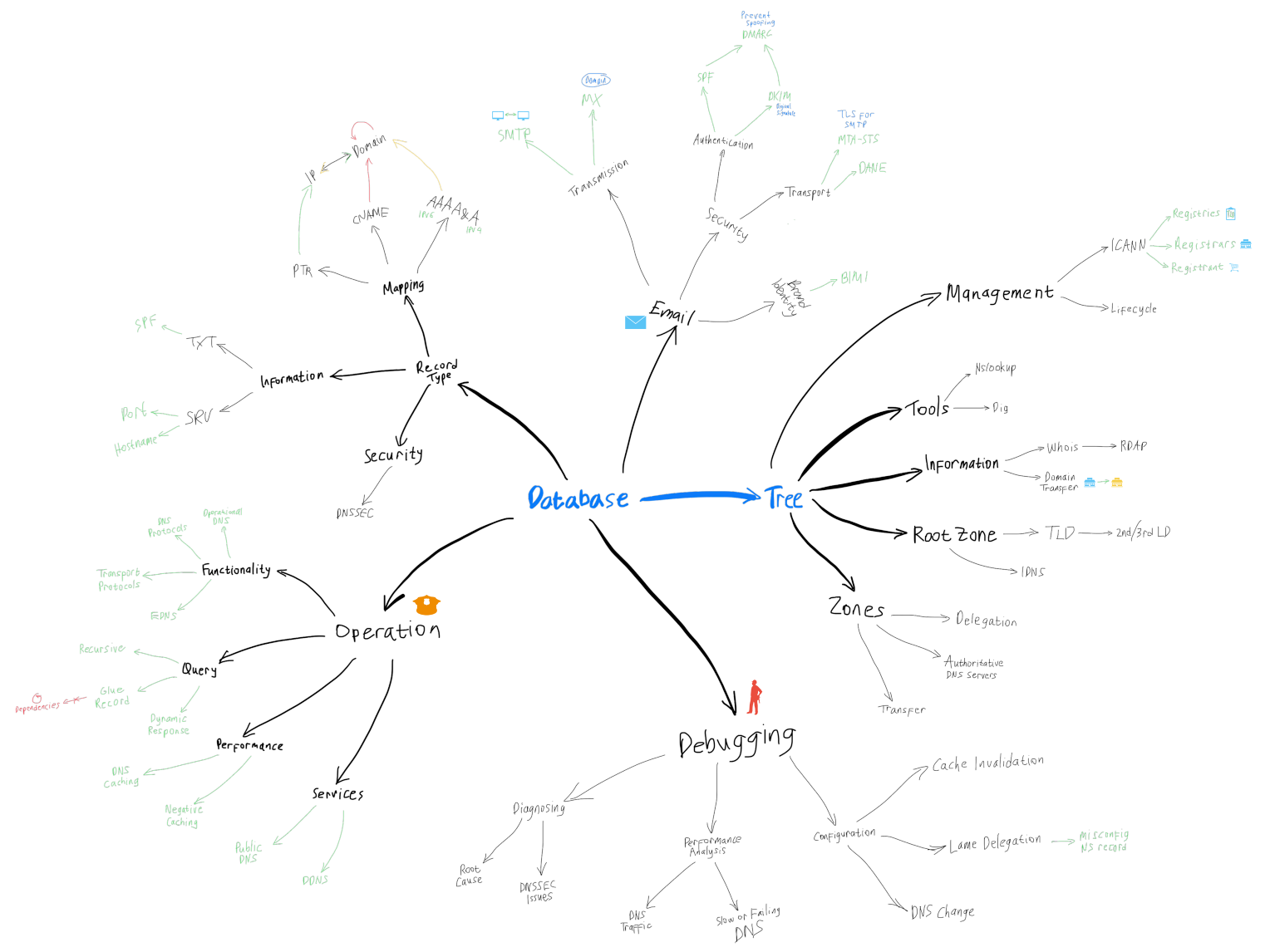
Shape like a tree
The DNS structure follows a hierarchical, tree-like system, starting from root servers and branching out through different levels of domain names.
Information
- WHOIS: A query-response protocol providing information about domain registrations. The newer RDAP (Registration Data Access Protocol) aims to modernize WHOIS with better features.
- Domain Transfer: The transfer of domain ownership between registrars follows strict policies set by domain authorities.
Management
ICANN
The Internet Corporation for Assigned Names and Numbers (ICANN) oversees global DNS operations, working with:
- Registries: Organizations that manage top-level domains (TLDs).
- Registrar: Companies that handle domain name registrations for users.
- Registrant: The individual or entity that owns a domain name.
Lifecycle
Domain names follow a lifecycle from registration, through active use, to expiration, renewal, or deletion.
Zones
Delegation
DNS delegation distributes the responsibility for managing different parts of the namespace to various authoritative DNS servers.
Authoritative DNS Servers
These servers provide the definitive answers for their designated zones, containing all DNS records for the zone. Readmore: How to find a domain’s authoritative nameservers
Zone Transfer
Zone transfers move DNS data between servers, often to synchronize secondary servers with the primary authoritative server.
Root Zones
TLD (Top-Level Domain): The highest level in the DNS hierarchy (e.g., .com, .org).
- ccLTD: Managed by a country. Readmore: ISO 3166
- gTLD: Managed by commercial or non-profit organization.
2nd/3rd LD: Second and third-level domains add further subdivisions, commonly representing specific websites or services.
IDNs (Internationalized Domain Names): Domains that include non-ASCII characters, enabling broader global use. Readmore: RFC 3492
Readmore:
Tools
nslookup and dig: These tools are essential for querying DNS information and diagnosing DNS issues.
Readmore:
Functioning like a database
The DNS (Domain Name System) operates as a vast, distributed database. It maps human-readable domain names to machine-recognizable IP addresses and other critical information for internet functionality.
Record Type
Each record type in DNS serves a distinct purpose, mapping different types of information. Readmore: DNS Record Types
Mapping
- A and AAAA: These records map a domain to an IP address. The A record handles IPv4 addresses, while the AAAA record supports IPv6, enabling connectivity across different IP versions.
- CNAME: This stands for Canonical Name, mapping one domain name to another, useful for aliasing one domain to another for better DNS management.
- PTR: The Pointer Record maps an IP address back to a domain, enabling reverse DNS lookups, often used in verifying the identity of IP addresses in email systems.
Information
- TXT: Text records can store any arbitrary text but are most commonly used to hold SPF (Sender Policy Framework) records, which specify which mail servers are allowed to send emails on behalf of a domain. Readmore: RFC7208
- SRV: Service records map hostnames to specific services and ports, critical for applications like VoIP (Voice over IP) or LDAP (Lightweight Directory Access Protocol).
Security
- DNSSEC: DNSSEC provides an additional layer of security to DNS by ensuring that responses to DNS queries are authentic and have not been altered. This is crucial in preventing attacks like DNS spoofing, where an attacker provides fake DNS data.
- Chain of Trust: DNSSEC operates using a hierarchical trust model known as the chain of trust. At the root of this chain are DS (Delegation Signer) records, which link parent and child zones in DNS, ensuring that the signatures on DNS records are valid. The DNSKEY record contains the public key used to verify the digital signatures of DNS records in a zone.
- Signs DNS Records: To ensure the authenticity of DNS data, RRSIG (Resource Record Signature) signs DNS records with a cryptographic signature. The signature can then be validated using the public key from the DNSKEY record, ensuring that the data hasn’t been tampered with.
- Denial of Existence: DNSSEC can also authenticate responses when a domain or record doesn’t exist. The NSEC (Next Secure) record lists the next available domain in a zone, proving that no domains exist between two records. NSEC3 and NSEC3PARAM add further security by providing hashed representations of the domain names, offering privacy and resistance to zone enumeration attacks, while still ensuring that non-existent domains are properly validated
Operation
DNS operates through complex protocols and functionalities to resolve domain names efficiently and securely.
Functionality
- Operational DNS: DNS servers around the world operate in a hierarchy, from root servers to local resolvers, ensuring the system remains available and accurate. Readmore: A toy DNS resolver
- DNS Protocols: DNS primarily uses UDP for faster, lightweight queries but falls back to TCP when necessary, especially for zone transfers or larger responses. Readmore: DNS Packet Structure, Format of a DNS packets
- Transport Protocols: TCP and UDP are the main transport protocols for DNS, with extensions like EDNS (Extension Mechanisms for DNS) supporting larger message sizes and additional features.
- Use port 53 : Do53 (UDP and TCP) and Oblivious DNS (ODNS)
- Use port 443 : DoH (HTTPS), Oblivious DoH and DNSCrypt
- Use port 853 : DoT (TLS) and DoQ (QUIC)
- Depends : TOR
- Readmore : Why might you run your own DNS server?
Query
- Recursive: A DNS resolver performs recursive queries by querying multiple servers on behalf of the client to find the correct answer. Readmore: The multiple meanings of “nameserver” and “DNS resolver”
- Glue Record: This is a crucial component in DNS delegation, used to avoid circular dependencies in the name resolution process. Readmore: Rethinking the Security Threats of Stale DNS Glue Records
- Dynamic Response: DNS responses can be dynamically generated based on request parameters, enabling more flexible and intelligent DNS behavior.
Performance
- DNS Caching: To improve performance, DNS servers cache responses, reducing the need to perform repetitive queries. Readmore: DNS “propagation” is actually caches expiring, The Maginot Line: Attacking the Boundary of DNS Caching Protection
- Negative Caching: DNS servers also cache negative responses (e.g., non-existent domain queries) to prevent excessive repeated lookup failures.
Services
- Public DNS: Public DNS services like Google Public DNS or Cloudflare provide faster and more secure DNS resolution compared to ISP-operated DNS.
- DDNS: Dynamic DNS allow domain records to be automatically updated when an IP address changes, useful for devices that don’t have static IP addresses. This ensures continuous access to resources like websites or applications even when the underlying IP changes.
- Round-robin DNS: This technique distributes traffic across multiple servers by rotating through a list of IP addresses associated with a single domain name. It is a simple form of load balancing where each request cycles to the next server.
- Weighted round-robin DNS: An enhancement of round-robin DNS, this method assigns different weights to each server based on their capacity. Servers with higher capacity receive more traffic, improving load distribution efficiency.
- Dynamic Load Balancing: A more advanced form of load balancing where DNS dynamically adjusts the server selection based on real-time data.
- (Weighted) Fewest Connections: DNS directs traffic to the server with the fewest active connections, ensuring that no single server becomes overwhelmed, and resources are used efficiently.
- Split-horizon DNS: A technique where different DNS responses are provided based on the requester’s source, typically internal vs. external networks. It is commonly used in proximity-based DNS, where users are directed to servers closest to their geographical location to optimize response times and reduce latency.
DNS is integral to the email transmission process, ensuring that emails reach their intended recipients.
Transmission
- SMTP: The Simple Mail Transfer Protocol governs how email servers send messages between one another.
- MX: Mail Exchanger records within DNS specify which mail servers should receive emails for a domain.
Security
Authentication
- Prevent Spoofing: DMARC is an email authentication protocol that uses SPF and DKIM (DomainKeys Identified Mail) to prevent email spoofing and phishing. SPF ensures the sending server is authorized, while DKIM verifies the email’s integrity through a digital signature. Readmore: DMARC
Transport
- MTA-STS: Mail Transfer Agent Strict Transport Security enforces the use of TLS (Transport Layer Security) for secure email transmission.
- DANE: DNS-based Authentication of Named Entities uses DNSSEC to ensure that TLS certificates are valid and properly authenticated. Readmore:
Brand Identity
- BIMI: Brand Indicators for Message Identification allow companies to display their logos in email inboxes, increasing brand trust and recognition through authenticated emails.
Debugging
Diagnosing and troubleshooting DNS issues is crucial for ensuring smooth operations.
Diagnosing
- Root Cause: Identifying the root cause of DNS failures often involves checking the flow of queries from resolvers to authoritative servers. Readmore: How do you tell if a problem is caused by DNS?, Some ways DNS can break
- Failing queries:
- Inbound/outbound firewall.
- Oversaturated network and DNS server.
- Misconfigured stub resolver, authoritative server and parent zone.
- Wrong response:
- Stale records in cache.
- Misconfiguration NS records and stub resolver.
- Failing queries:
- DNSSEC Issues: Misconfigurations in DNSSEC can result in DNS failures due to authentication issues. Readmore: Troubleshooting
Performance Analysis
- DNS Traffic: Analyzing DNS traffic helps in understanding performance bottlenecks or detecting abnormal activity, such as DDoS attacks. Readmore: Capture Network Logs with Chrome
- Slow or Failing DNS: Performance issues might arise from overloaded servers, poor caching configurations, or network issues. Readmore : What happens when you update your DNS?
Configuration
- Cache Invalidation: Caching can lead to outdated responses, invalidating the cache forces DNS to retrieve fresh information.
- DNS Change: Changing DNS configurations may introduce issues, such as wrong IP mappings or delays due to TTL (Time-to-Live) values.
- Lame Delegation: This occurs when a DNS server is listed as authoritative for a domain but cannot respond to queries due to misconfiguration of NS (Name Server) records.
What’s next?
- Why is DNS still hard to learn?
- TuDoor Attack: Systematically Exploring and Exploiting Logic Vulnerabilities in DNS Response Pre-processing with Malformed Packets
- Attacking with Something That Does Not Exist: Low-Rate Flood with ‘Proof of Non-Existence
- DNSBOMB: A New Practical-and-Powerful Pulsing DoS Attack Exploiting DNS Queries-and-Responses
- The KeyTrap Denial-of-Service Algorithmic Complexity Attacks on DNS
- TsuKing: Coordinating DNS Resolvers and Queries into Potent DoS Amplifiers
- Information-Based Heavy Hitters for Real-Time DNS Data Exfiltration Detection and Prevention
- Timeless Timing Attacks and Preload Defenses in Tor’s DNS Cache
- Securing name resolution in the IoT: DNS over CoAP
- A New Class of DNS Vulnerabilities Affecting Many DNS-as-Service Platforms
Resource
- DOMAIN NAMES - CONCEPTS AND FACILITIES
- DOMAIN NAMES - IMPLEMENTATION AND SPECIFICATION
- DNS Extensions to Support IP Version 6
- The DNS course for developers
- https://x.com/b0rk/status/1467585993138229248
- Julia Evans’s blogs and zines
- How Does DNS Work?